AWS (Amazon Web Services) provide a robust cloud platform to host your application, infrastructure but security is something you got to take care of yourself.
There are many incidents where attacker hacks the AWS account and abuse it for their purpose or just for fun.
I came across this post on Quora, where the user’s AWS account was hacked and received a $50,000 bill!
Single sensitive information leakage can cost you heavily and damage your reputation. So how do you ensure you’ve taken all the necessary steps to protect the AWS account?
One way you can do is to follow industry security guidelines manually, which is time-consuming and prone to human error. Or you can use the following SaaS (Software-as-a-service) to automatically audit your AWS platform for the security loophole and misconfiguration.
Note: Below vulnerability scanner are specifically for AWS Cloud and not for website or web applications.
Let’s explore what options we have…
Update: using Google Cloud Platform (GCP)? Check out GCP security scanner.
AWS Config
AWS Config is an effective tool for assessing, evaluating, recording, auditing configurations of the resources in your AWS environment. It simplifies security analysis, compliance auditing, operational troubleshooting, and change management.
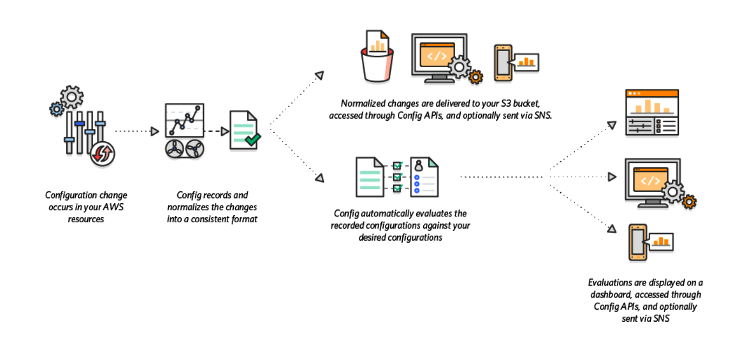
key features include
- Provide continuous monitoring, assessment, and recording of the resource configurations.
- Enables you to discover resources, record the configurations in your AWS environment, and keep important information about their changes and deletions.
- Automate the evaluation of the recorded AWS resource configurations against expected values.
- Quickly troubleshoot operational issues by determining the recent resource configuration changes causing the problems.
- Supports change management processes by keeping track of the created, updated, and deleted resources while notifying you about any modification.
Intruder
Intruder is a modern vulnerability scanner, designed from day one to work seamlessly with the three major cloud providers, AWS, GCP, and Azure. It is enterprise-ready and offers a government & bank-level security scanning engine without complexity.
Intruder makes cloud security a breeze by allowing you to easily monitor your cloud systems, discover new assets, and automatically synchronize your scan targets. It continuously observes what you expose to the Internet and sends notifications about important changes, such as when open ports and services change, which, if unnoticed, could lead to a security breach.
Unlike some cloud-only vulnerability scanners though, Intruder is able to seamlessly monitor your traditional edge networks, web applications, and internal environments too, for an all-in-one effortless vulnerability management experience.
Its robust security checks include identifying:
- Missing patches
- Misconfigurations
- Web application issues such as OWASP top 10, SQL injection & cross-site scripting
- CMS issues
Intruder proactively scans your systems for new vulnerabilities, keeping you protected against the very latest threats. This kind of proactive action is essential for busy teams that don’t have time for manual research.
You can give Intruder a try for 30 days for free.
Astra Pentest
Astra is a hacker-style VAPT platform that combines automated & manual pentest to create a one-of-a-kind pentest platform. It offers an interactive dashboard where you can monitor the audit and see the detailed analysis for each discovered vulnerability, along with the recommended steps to fix those vulnerabilities.
Astra offers both white box & black box scanning of your AWS infrastructure. The security review includes scanning your IAM policies, EC2 instances & other services like S2, RDS, Lambda, etc.

The in-depth Pentest by Astra ensures your entire AWS infrastructure is watertight and secure. Other notable features of Astra Pentest are:
- Cloud Configuration Review of AWS configurations to systematically check for any vulnerabilities and ensure the latest, best security practices are followed.
- Business Logic Error Tests to assess the susceptibility of the AWS infrastructure to privilege escalation or bypassing of security restrictions.
- Scan Behind Logins using Astra’s Chrome extension to scan areas of web applications hosted on your AWS to find any internal vulnerabilities.
- Risk-Based Vulnerability Management based on actionable risk scores, POC videos, and contextual collaboration for quick patching of vulnerabilities.
- Compliance Scans for PCI-DSS, ISO27001, HIPAA, GDPR, SOC2, etc.
- Penetration Tests by security experts have over 8000+ test cases to aid in the detection of vulnerabilities.
- CI/CD Integrations of web vulnerability scanners with the likes of Slack, Jira, GitHub, GitLab, and more are available to make a move from DevOps to DevSecOps seamless.
- Actionable vulnerability reports provide extensive vulnerability details, actionable risk scores based on contextual data, and CVSS scores for easy remediation.
- Collaborative Dashboards allow collaboration between the pentesting team and the development team for quick vulnerability management.
- Industry-recognized Pentest Certificates by Astra are publicly verifiable and showcase the reliability of services.
- 24/7 Expert Customer Support aiding in the clearance of customer queries through the dashboard or the support team within 24 hours. Extensive Slack integration to get alerted and manage vulnerabilities within Slack.
- Rescans are provided to ensure all vulnerabilities have been mitigated.
Choose among the varied packages provided by Astra to meet your AWS security requirements with ease!
Cloud Custodian
Cloud Custodian is a flexible open-source rules engine for managing the AWS cloud resources and accounts to ensure security and policy compliance. This allows you to manage and optimize security, costs, and governance of your AWS cloud environment.
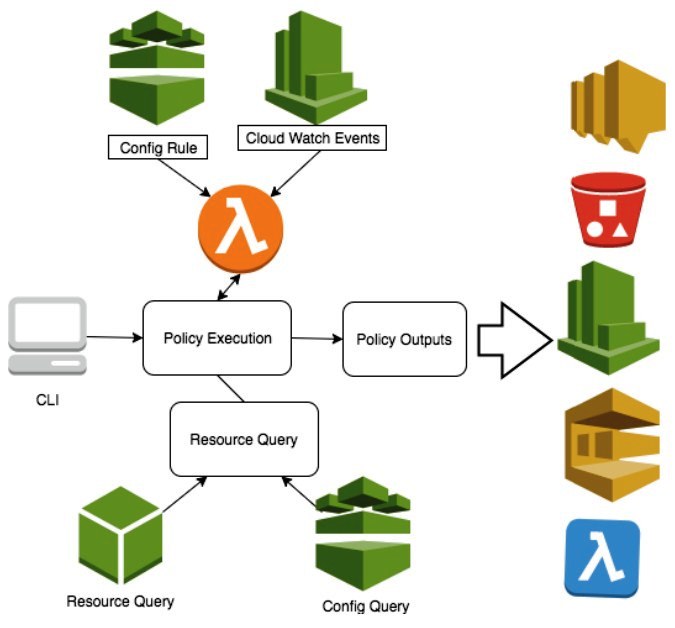
Cloud Custodian key features
- Providing real-time compliance checks and report on violations.
- It allows you to control costs by managing the unused and off-hour resources.
- A flexible deployment that allows you to run the tool on an instance, locally or serverless.
- Ability to manage users and enforce security policies in the AWS cloud environment
- Consolidates several functions into a flexible, lightweight tool with unified metrics and reporting.
Prowler
Prowler is an AWS account’s security configuration assessment, auditing, and hardening tool that also checks compliance with the CIS AWS Foundations security standards. Further, the tool performs over 100 additional checks, including HIPAA, GRDR, forensics readiness, trust boundaries, and more.
The Prowler command-line tool covers several identity and access management practices, logging, monitoring, and other security assessment activities on Amazon accounts such as the Redshift, CloudFront, ElasticCache, Elasticsearch, API Gateway, and others.
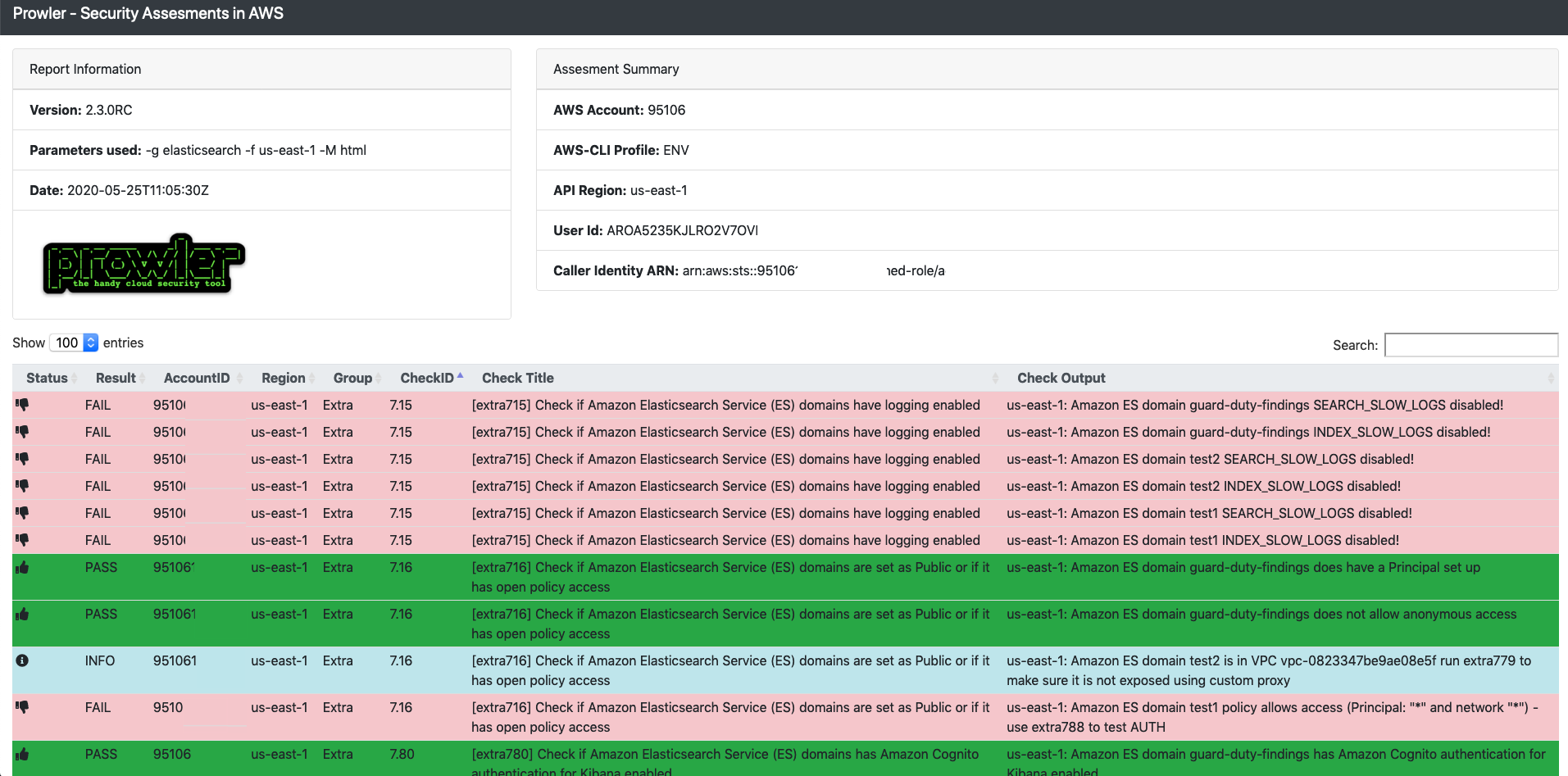
Highlights
- Comprehensive assessment of the security posture of your AWS accounts
- Integrate with other tools such as Cloud Security Suite, Telegram, etc.
- Check multiple AWS accounts in parallel
- Run specific checks without having to perform the entire test
- Identify assets not covered by security systems.
Cloudmapper
Cloudmapper is an open-source tool that enables you to analyze and build an interactive visualization of assets, services, and other components in your AWS environment.
Generally, the tool allows developers to check and understand the type of environments they have built. It does this by collecting the data from your AWS accounts and then converts it into a browser-accessible format.
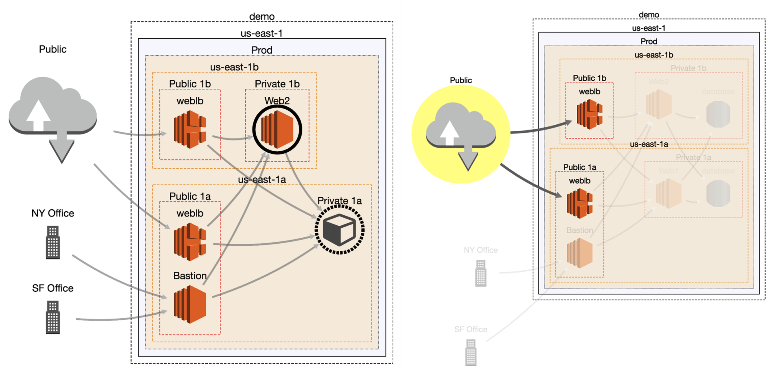
Typically, the Cloudmapper outputs the analysis in the form of network diagrams for the AWS cloud environments. The visual presentation enables you to understand your accounts, how they relate to cloud resources as well as establish if there are misconfiguration or other issues.
This allows you to
- See the complexity of the AWS account, size, and regions it serves, etc.
- Establish the resources that can communicate with each within the environment
- Perform security audits, and easily share the analysis information.
- Identify publicly exposed resources
Cloud Reports
Cloud reports from Tensult is a node.js based open source tool for collecting and analyzing a wide range of information from various cloud components. The tool compares the findings against the best practices.
It then generates reports, which are usually in HTML, CSV, JSON, or PDF, to show the different AWS services running along with the best practices you should follow. This also contains issues it has identified as well as their impact on your services.
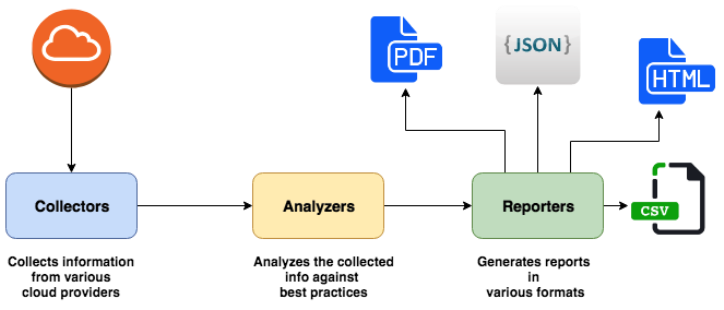
The HTML reports are usually accessible via a web browser, while those in JSON, CSV, and PDF are stored on a folder. Each of these has a timestamp for easy identification and access when running multiple scans.
AWStealth
AWStealth is a security that tool teams use to discover the most privileged entities in the AWS cloud environment. The scan results show the users with excessive, risky, or sensitive permissions. And this enables the security teams to identify the most privileged accounts that they need to properly secure from potential attacks and exploits.
Typical AWS entities with sensitive privileges that should be on the radar include the straight-forward admins as well as the risky shadow admins.
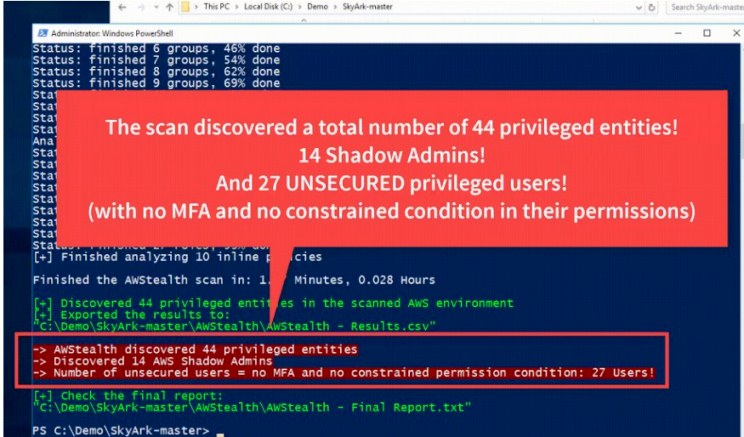
The AWStealth thus enables the security teams to prevent threats arising from the shadow admins and other privileged account vulnerabilities.
Salesforce Policy sentry
Policy sentry is an AWS IAM privilege management tool. It has an IAM least privilege policy generator, an audit mechanism, and an analysis database. The tool compiles database tables according to the AIM documentation about the resources, actions, and condition keys. It then uses this data to create IAM least-privilege policies.
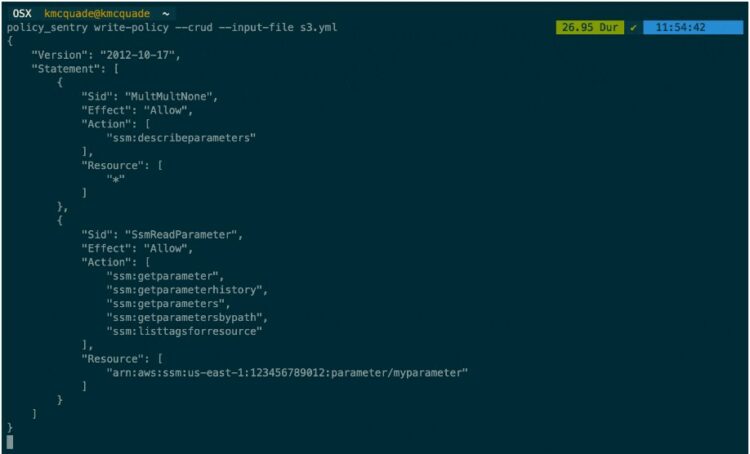
Highlights
- Simplifies writing of security-based IAM policies
- Limit the impact of a security breach since an attacker who accesses the system with a user’s credentials will only have the least privileges that cannot perform administrative tasks.
- Automatically and easily create secure IAM policies hence eliminate the tedious manual based tests that require higher levels of technical expertise.
Komiser
Komiser is a comprehensive inspection and analysis tool that helps you to monitor and control expenses for your AWS cloud platform. The open-source cost optimization tool can inspect the cloud platform and check for a wide range of configuration and cost issues. This discovers any hidden costs and provides you with recommendations to help you save and remain within budget.

Key features
- It enables you to analyze and manage usage, cost, security, and compliance of your AWS platform from one place and in real-time.
- Provides you with the visibility of all the services you are using
- Identify and address vulnerabilities as well as compliance issues in the AWS configurations and environment.
- Get visibility into all your services and how to control costs and maximize ROI.
Alien Vault
Alien Vault USM (Unified Security Management), one of the market leaders in SIEM (Security Information and Event Management) solution for AWS.
USM is a single security monitoring platform to provide visibility of what’s happening so you can take full control of AWS cloud and manage risk.
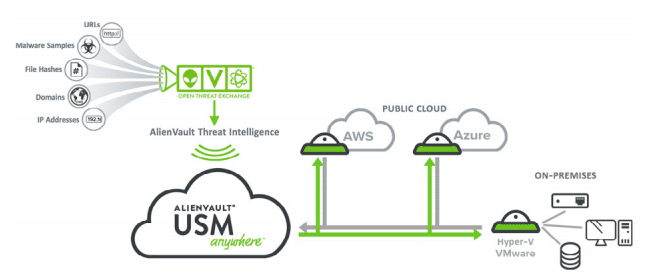
Some of the essential inbuilt features are:
- Monitoring & alerting for S3 & ELB logs, CloudTrail, File integrity, VPC flow
- Event correlation
- Asset discovery using network, API, software & service
- Vulnerability scanning for network, cloud & infrastructure
- Intrusion detection for cloud, network, host
Alien Vault provides actionable threat intelligence, which is powered by OTX (Open threat intelligence). It works with Amazon shared responsibility model. With the help of AWS-native sensors, you can detect whenever suspicious instance provisioned, new user, get created, security group modified, etc.
CloudSploit
CloudSploit is capable of detecting hundreds of threats in the AWS account by automated security scanning and configuration monitoring.
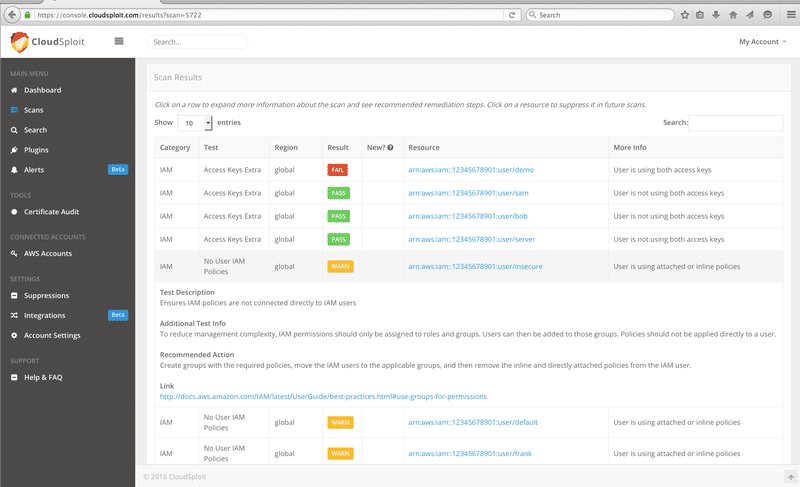
You can use CloudSploit in every AWS region, and it’s not just provide scanning results but also the recommendation to fix the issues.
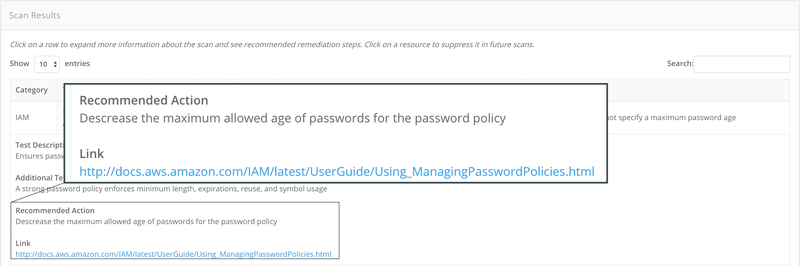
CloudSploit offers API, which is useful if you are looking to integrate security scanning in your application. A good thing is you don’t need to install any agent on your server to be monitored.
You can get it started in FREE for unlimited on-demand scans. And if you are looking for an automated scan, risk finding emails, real-time event streams, etc. then you got to pay for it.
Skyhigh
Skyhigh, provide comprehensive security monitoring, auditing, compliance, and remediation for AWS infrastructure.
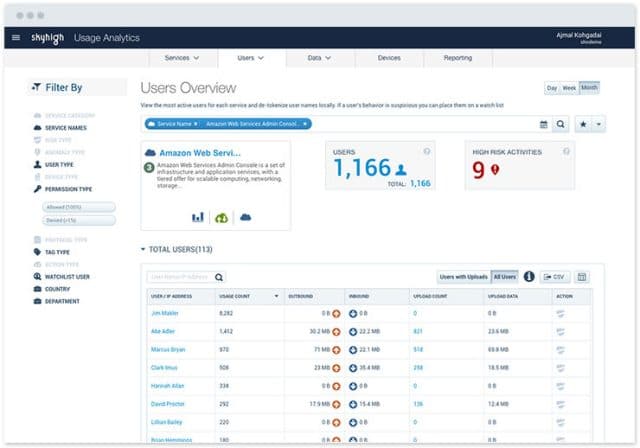
Some of the essential features of Skyhigh are:
- Complete audit trail of users activity
- Detect insider threats, compromised accounts
- Compliance, user permission, and security configuration auditing
- Enforce data loss prevention policies
- Cloud activity monitoring
- IAM, account access, user behavior analytics
- Integration with SIEM and IDM
- Multi-tier remediation
It supports a forensic investigation and automatically includes threats resolution data into self-learning for improved detection accuracy.
Qualys
Qualys, one of the industry leaders in vulnerability scanner platform for website, network provide total visibility of AWS cloud to secure and compile from internal and external policies.
Qualys provides a cloud agent that can be installed either on EC2 or at the source into AMI for automated asset discovery, classification, monitoring, and vulnerability remediation.
ScoutSuite
ScoutSuite is a python based open-source tool to view the security posture of the AWS environment. It fetches CloudTrail, S3, AMI, EC2, etc. data and reports it in HTML format.

Risk items are categorized automatically and denoted in danger and warning with red and yellow color, respectively.
Alert Logic
Improve your AWS security posture with Alert Logic Cloud Insight. Alert Logic is capable of inspecting full-stack infrastructure, including network, open-source, enterprise software against more than 90000 known vulnerabilities.
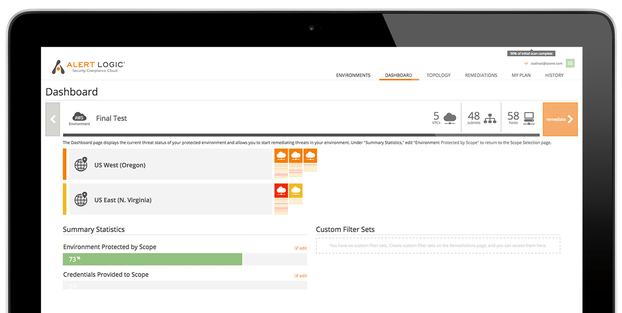
Some of the essential Alert Logic key capabilities are:
- Visual topology map for faster prioritization
- Remediation prioritization based on the severity of vulnerabilities
- Track improvement trends
- Easy integration with SecOps & DevOps using RESTful API
- Agentless comprehensive checks
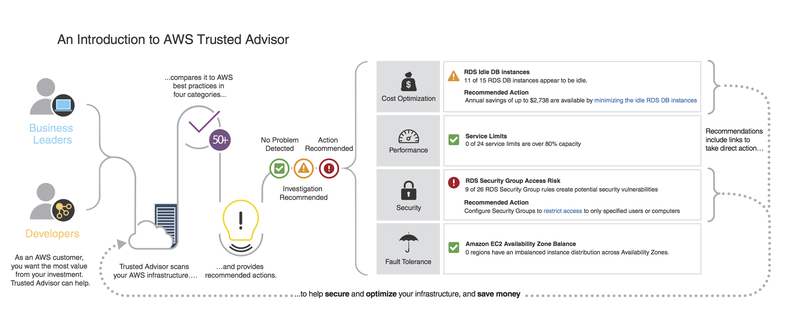
AWS Trusted Advisor
The list won’t be complete without mentioning AWS Trusted Advisor, a real-time guide to improve security, reduce cost by following AWS best practices.
Conclusion
AWS provides security on core infrastructure, but what you deploy, configure is your responsibility. I hope above listed AWS security scanning solution helps you to keep your AWS cloud environment secure & cost-effective.

















